Read time: 3 mins
Market research companies are faced with varying challenges and security threats when it comes to keeping their research data secure. Over the last two years, there have been many breaches exposing millions of data records as cybercriminals have been targeting both the public and private sectors. According to IBM’s 2019 Cost of a Data Breach Report, the average cost of a data breach worldwide is $3.9 million. For the United States, that number soars to $7.91 million.
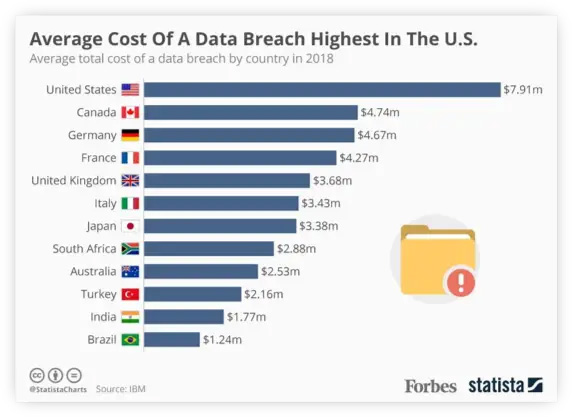
Source: https://www.statista.com/chart/9918/the-price-tag-attached-to-data-breaches/
Key Takeaways
- Market research companies face growing cybersecurity threats, with breaches costing millions annually.
- Protecting both data in motion (transferred data) and data at rest (stored data) is essential.
- Strong security measures—such as intrusion detection systems, regular audits, and penetration testing—help mitigate risks.
- Trust and compliance with industry best practices are critical for maintaining data security and participant confidence.
The burden of responsibility is widening as many international regulators are now holding organizations liable for any privacy or security breaches. As custodians of sensitive client data, market research companies have a responsibility to minimize the security risk for data both in motion and at rest.
Data in motion, as its name suggests, refers to information being moved from one location to another across the internet, along networks, or from storage devices or the cloud. Protection methods are particularly critical because this data in transit tends to be thought of as less secure than data at rest, which is information simply stored or archived on hard drives, devices, or networks.
Protecting data is critical not only for its own obvious sake, but also to reassure potential survey participants who might be apprehensive about participating in your market research project due to being aware of recent data breaches in other sectors.
Some recommended measures to be implemented include:
- Providing staff with cybersecurity tools to ensure ongoing compliance with best practice policies and procedures.
- Lowering risk exposure by implementing technology such as intrusion detection systems (IDS), intrusion protection systems (IPS), honeypots, and firewalls.
- Regularly monitoring and auditing security procedures to address evolving cyber threats.
- Implementing detailed security policies that outline procedures, rules, and roles so all staff members understand that data privacy and security are priorities (e.g., handling procedures, usage, privacy, social media, and user responsibilities).
- Staying informed about cyber-threat news, updates, and applicable security patches.
- Investing in data-breach or cybersecurity insurance.
- Conducting penetration testing—also known as “ethical hacking”—to identify security vulnerabilities in computer systems or networks before they can be exploited.
Perhaps one of the most important data security recommendations comes down to always ensuring you are working with people whose approaches and practices you can trust. The Logit Group is continually implementing new measures that comply with industry best practices and address client concerns and requirements about data security and privacy while adhering to data protection laws. Contact us today to learn more about our research execution services.
FAQs
Market research companies are at risk of cybersecurity threats, including data breaches, which can expose millions of sensitive records. These breaches often result in significant financial costs, with the average cost of a breach reaching millions of dollars, especially in the U.S.
Companies can protect data in motion (transferred data) and data at rest (stored data) by implementing measures like intrusion detection systems, firewalls, regular audits, and penetration testing. Staff should also be equipped with cybersecurity tools to ensure compliance with best practices.
Trust and adherence to industry best practices are essential for maintaining data security and participant confidence. Market research companies must demonstrate their commitment to data privacy by working with reliable partners and staying updated on security threats and necessary compliance standards.





